Cybersecurity Monthly Report (December 2023)
Ex ante joint defense and monitoring
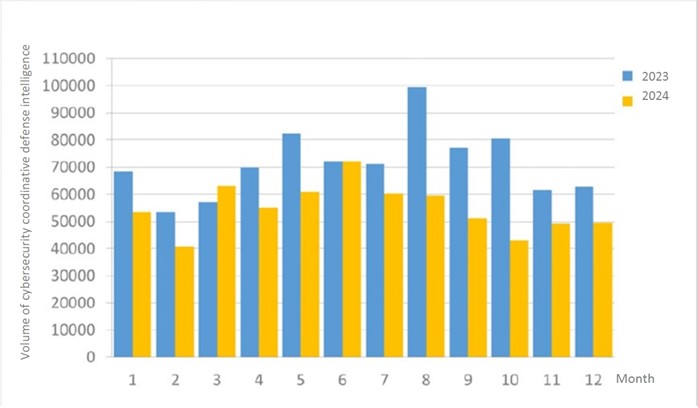
A total of 49,581 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of nearly 500 from the previous month), analyzing the types of identifiable threats. The top identifiable threat was information collection (49%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering. This was followed by hacking attempts (24%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (11%), most of them involving unauthorized access to systems or acquisition of system/user privileges. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
Upon further compilation and analysis of the joint defense information, it was discovered that hackers had recently stolen e-mail information from compromised computers, including e-mails between the general public and an agency. Hackers use contents or subject lines of stolen public e-mails as baits to send social engineering e-mails containing malicious attachments to agency personnel in an attempt to trick agency recipients into opening the malicious attachments, thereby allowing them to plant backdoor programs and steal computer information. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
In-process reporting and responding
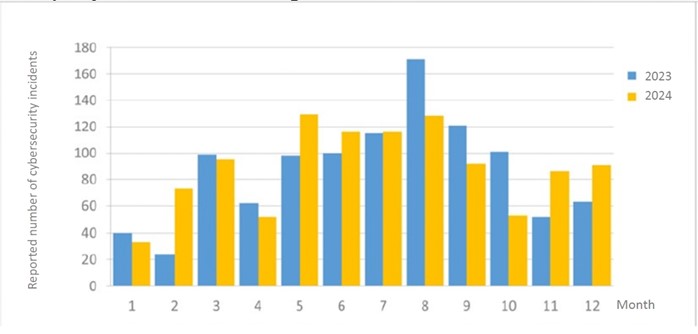
A total of 91 cybersecurity incident reports were submitted this month, an increase of 44.44%compared with the same month last year. Analysis of the detection information revealed that they were mainly due to information devices from multiple agencies attempting to download malicious programs or connecting to seemingly malicious programs. The number of these reports accounted for 49.45%.In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
Post information sharing
According to the agency's cybersecurity incident report, it was found that the network surveillance management login interface can be accessed on the public network, exposing the equipment to the risk of brute-force attacks and vulnerability exploitation. Some equipment from agencies has been hacked, where they were connected to a relay station to download malicious programs. Subsequently, the agency assessed whether the aforementioned network surveillance equipment required public access, and disconnected or restricted the equipment to internal IP access to reduce cybersecurity risks.
Information equipment management interface that is open to the public allows administrators to remotely operate the system in real time. However, if device access rights are not restricted, hackers can launch a brute-force attack on the login interface or exploit vulnerabilities to invade the system. In addition, the updating of IoT devices (such as monitors and printers) is often neglected, and if they are open to external access, they may become the main targets of hackers. It is recommended that when setting up the device management interface, agencies should restrict access rights to only allow internal IP access; the use of multi-factor authentication methods should be evaluated to be added to decrease the risk of system intrusion.