Cybersecurity Monthly Report (June 2024)
Ex ante joint defense and monitoring
A total of 70,641 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of 5,835 from the previous month). Analyzing the types of identifiable threats, the top identifiable threat was information collection (43%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering. This was followed by intrusion attacks (22%), most of them involving unauthorized access to systems or acquisition of system/user privileges; and hacking attempts (20%), which were mainly attempts to hack unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was discovered that hackers had recently sent social engineering e-mails with the subject line “Updates to Government Accounts” and with content designed to exceed the storage limit of users’ e-mail accounts in order to attack government agencies. Upon inspection, it turned out that the hackers had embedded a URL of a third-party cloud platform in the e-mails to entice recipients to click on the URL and disclose sensitive information. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
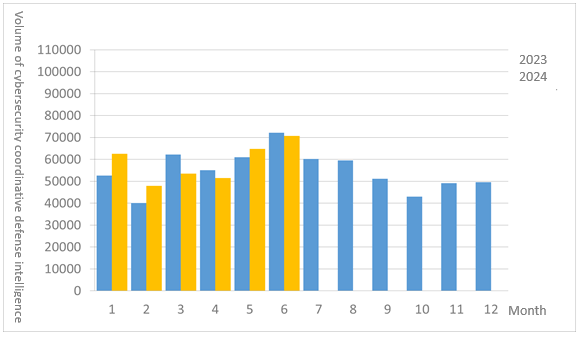
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 152 this month (an increase of 1 from the previous month), an increase of 31.03% compared to the same period last year. This is mainly due to the relatively high number of successful attacks related to the exercises this month, including injection attacks, insecure configuration settings, and encryption mechanism failures. The attacks accounted for 50% of the total number of reports this month. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
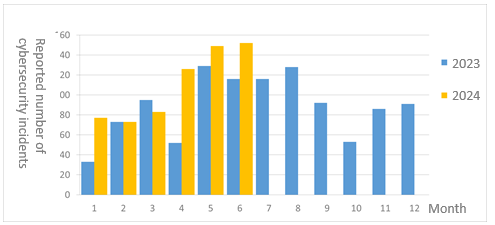
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month, an agency discovered that its Facebook fan page had been hacked and inappropriate images had been posted on the page’s wall. Upon investigation, it turned out that the password for the fan page administrator’s account was set too simple. The hackers cracked the password, set their account as administrator and removed other administrators. As a result, the agency was unable to log in and change the content of the fan page. A complaint was subsequently filed with Facebook to take down the hacked fan page, and a new one was created.
Additional Reference:
Government agencies typically use social media platforms (Facebook, Instagram, Line, or Youtube) as a channel for interacting with the public to communicate policy information in real time and encourage participation in public affairs. However, agencies should ensure that they follow information security guidelines and establish mechanisms to manage accounts on social platforms. This should include the following: Setting complex passwords, enabling two-factor authentication, ensuring that accounts on social platforms for official use are not mixed with private accounts, and setting up notifications of abnormal logins. Agencies should also regularly review the list of administrators to ensure that only employees with current operational needs are authorized to manage official fan pages so as not to jeopardize the agency’s reputation and credibility.