Cybersecurity Monthly Report (September 2024)
< Overall Threat Trend >
Ex ante joint defense and monitoring
A total of 78,515 pieces of government agency cybersecurity joint defense intelligence were collected this month (a decrease of 11,995 from the previous month). Analyzing the types of identifiable threats, the top one was information collection (41%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering; followed by intrusion attacks (25%), most involving unauthorized access to systems or acquisition of system/user privileges;and intrusion attempts (18%), most dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently used a ProtonMail free mail service account to launch a spear-style social engineering attack to the business windows for specific agencies with a malicious file reflecting a water pollution issue and a fake public pollution petition statement, to trick a target recipient into opening a malicious file through a public service related subject. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
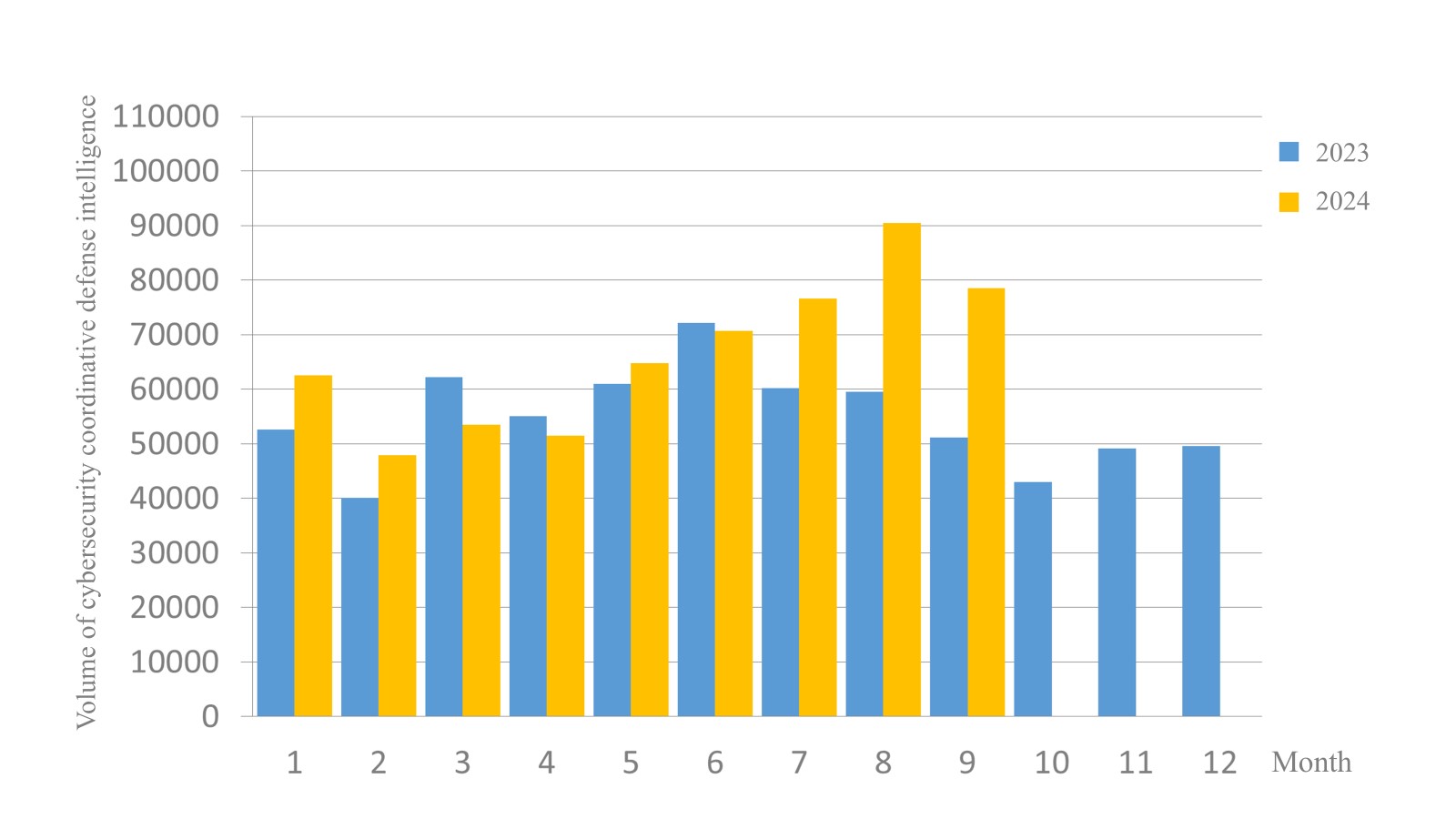
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 213 this month (an increase of 38 from the previous month), a 2.32-fold increase compared to the same period last year. This is due to the high number of successful attacks related to military exercises. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2. The main reason for the slowdown or interruption of website service was due to a number of agencies under the attack of blocking services, which accounted for 14.08% of the total number of reports for this month. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
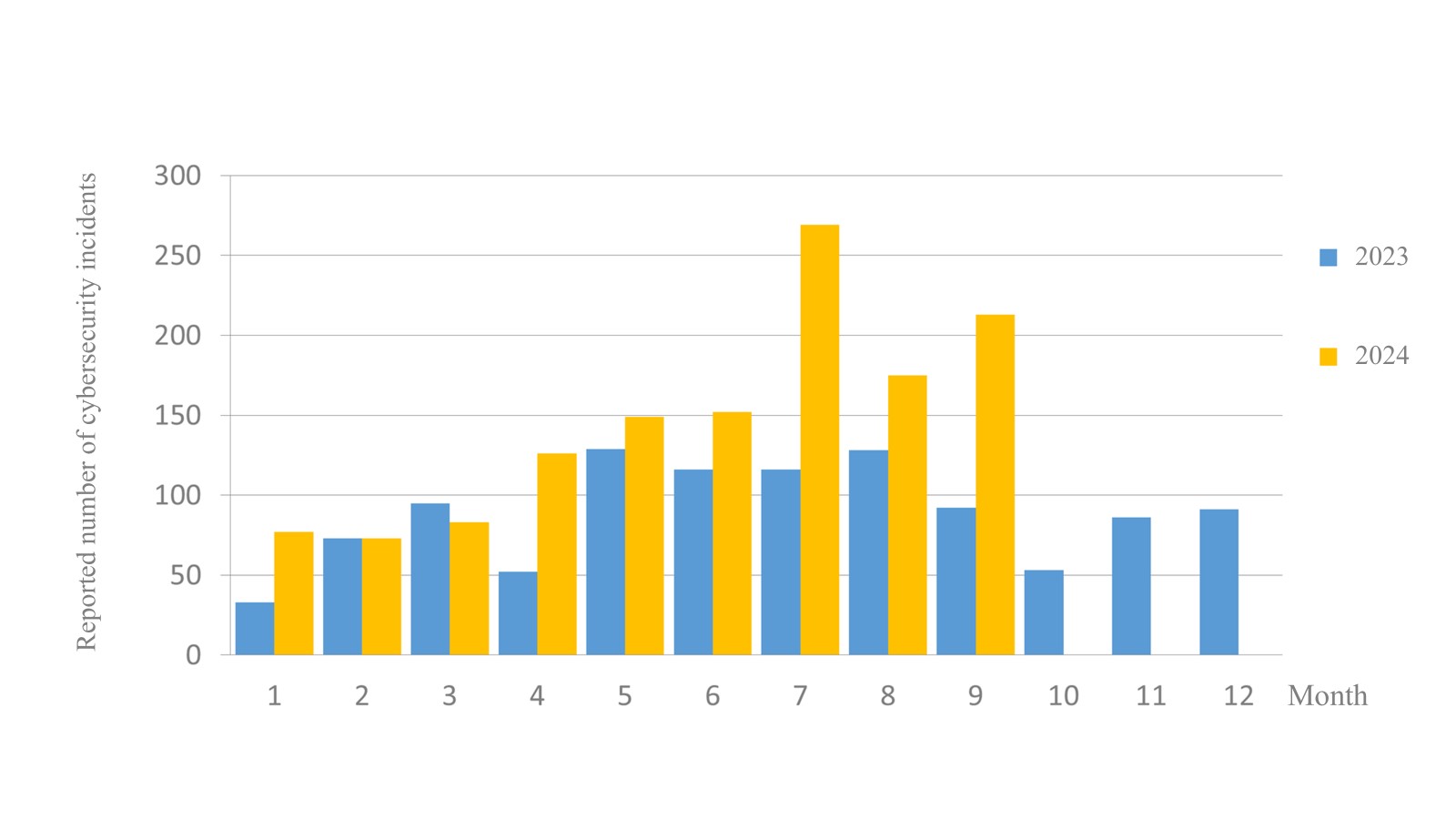
Figure 2 Number of cybersecurity incident reports
Post information sharing
This month, the National Institute of Cyber Security Research found that the documents provided by several governmental agencies on their websites have the risk of personal data leakage. To provide convenience for the public to use the website services, the documents provided by the abovementioned agencies include the actual application forms or examples of operation screens, and the sensitive information of some images is only masked by adding black boxes or other image layers, while the complete image information of the underlying layer is still retained in the documents, so that interested parties can use make copies of the underlying layer of the images and store them in other documents through Adobe Reader, and then further view the masked contents. Upon receipt of the notification, the agency has removed the relevant files and uploaded them with appropriate masking to minimize the risk of data leakage.
Additional Reference:
Government agencies must comply with the relevant regulations of the "Personal Data Protection Act" by implementing strict data management measures for sensitive personal information to ensure that collected data is not leaked, altered, or misused. Prior to the public release of any documents containing personal data, a comprehensive review should be conducted to confirm that personal data has been removed or adequately masked. Furthermore, regular cybersecurity training should be provided to improve staff awareness of personal data protection and to ensure that they are familiar with proper data masking procedures. This will effectively prevent similar incidents from happening again in the future, and safeguard data confidentiality, and maintain the reputation of the agencies.