Cybersecurity Monthly Report (May 2025)
Cybersecurity Monthly Report (May 2025)
<Overall Threat Trends>
Ex ante joint defense and monitoring
A total of 92,632 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of 19,844 from the previous month). Analyzing the types of identifiable threats, the top one was information collection (35%), mainly obtaining information through attacks such as scanning, detection, and social engineering, followed by intrusion attacks (34%), most involving unauthorized access to systems or acquisition of system/user privileges, and intrusion attempts (20%), mainly dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently been impersonating HiNet service agents and falsely claiming insufficient storage space of hacked HiNet email accounts. Social engineering emails containing phishing links were sent to attack government agencies. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
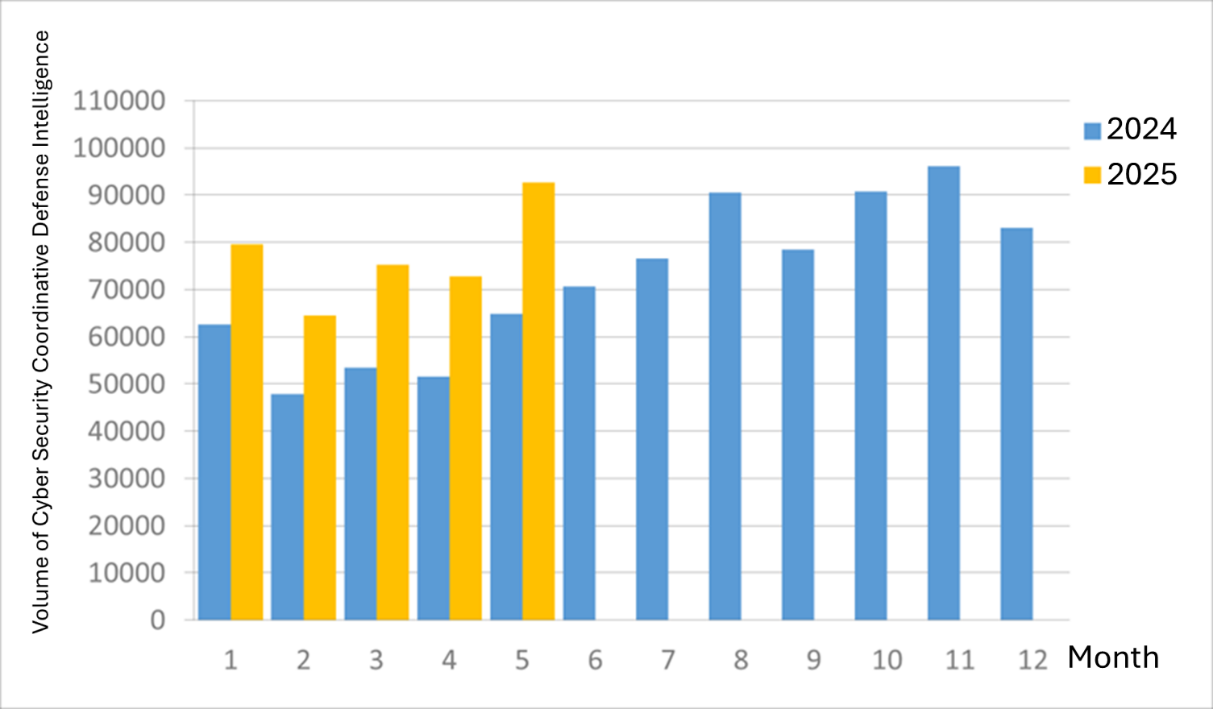
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 144 this month (an increase of 64 from the previous month), a 3.36% decrease compared to the same period last year. This month, there were more successful cases of attacks in exercises. These resulted mainly from unsafe configuration setting, followed by injection attacks and encryption mechanisms, accounting for 58.33% of the reported incidents this month. The statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
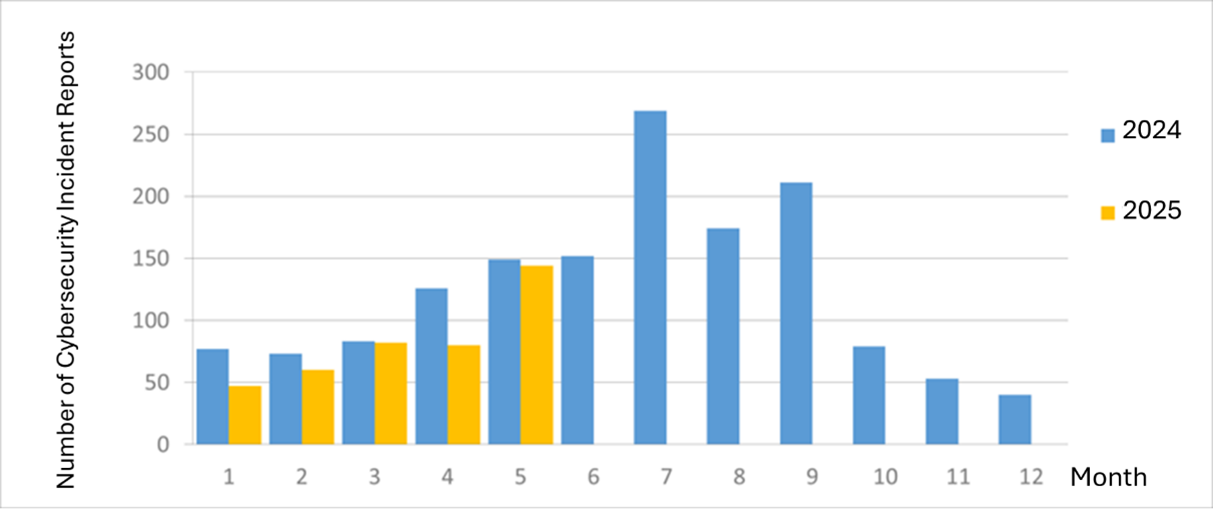
Figure 2: Statistics of cybersecurity incident reports
Post information sharing
This month, a wrong setting was discovered on the website of a government agency. The account number and password were delivered through web address (GET) in a clear message, which was also recorded on web log and could be accessed by external visitors. Thus, hackers obtained account number/password and logged in for access to internal information successfully. The agency has conducted resetting and confirmed that no large amount of information was accessed in the incident.
During the period of cyber offensive and defensive exercise (CODE), the National Institute of Cyber Security (NICS) found that unsafe configuration setting on the websites of many government agencies. This resulted in external access to information (phpino, .htaccess, web.config) that are not supposed to be opened to external access. Information such as system structure, directory path, current version, access control may be disclosed, increasing the risk of system attack and intrusion. With the receipt of notification, the agency has completed operations of remedy by removing redundant webpages and enhancing the measures of access and control on website server in order to reduce potential cybersecurity risk.
【Additional Reference】
Before attacks are launched, attackers often detect and collect system information, configuration vulnerability and account number of target websites as basis for attacks. If open directory and access file permission of websites are not under control, it may lead to the leak of web log file or setting file. Attackers may have obtained more knowledge on system structure and potential vulnerability, leading to a higher percentage of successful attacks. Agencies are recommended to remove redundant webpage information (i.e. phpinfo), impose strict control on website directory permission and not to place web log or setting file in the directory for external access. Regular virus scan is also suggested on website directory for inspection on any unauthorized or suspicious path in order to reduce the risk of attack that results from extra information on system.